Having Mac problems? Before trying more complex solutions, restart in safe mode — your Mac’s stripped-down troubleshooting environment. It disables non-essential software and clears system caches to help identify and resolve common issues.
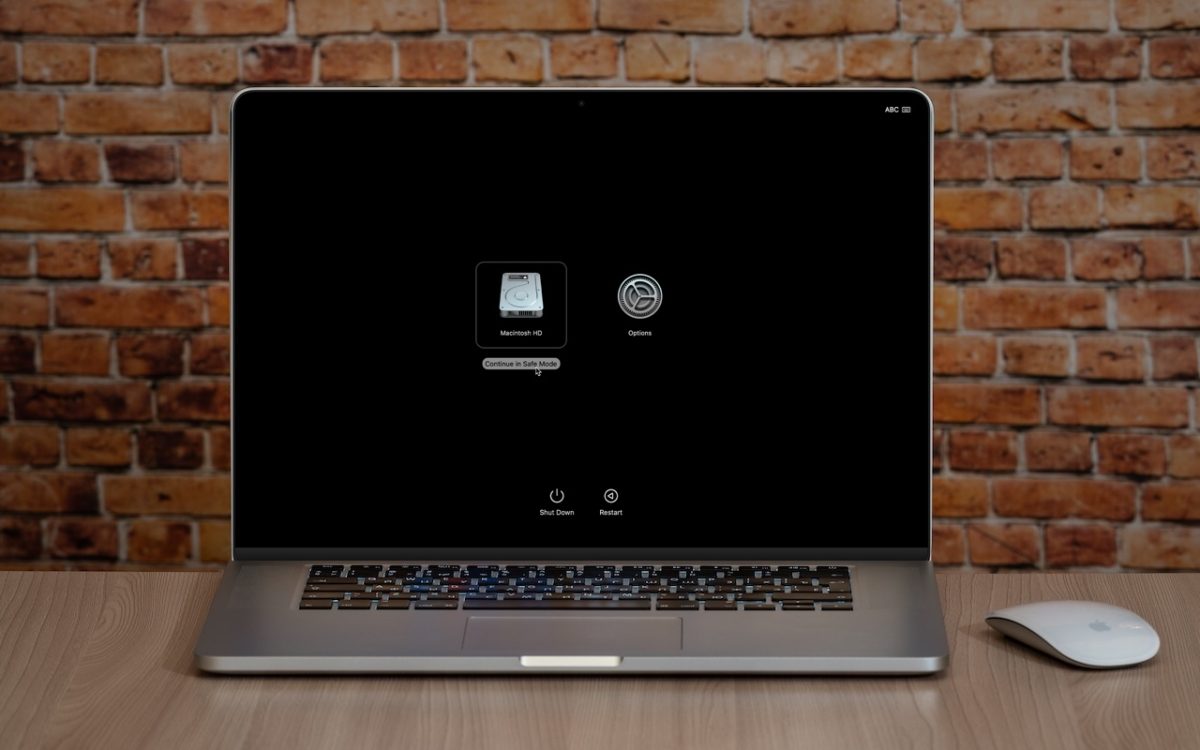

Having Mac problems? Before trying more complex solutions, restart in safe mode — your Mac’s stripped-down troubleshooting environment. It disables non-essential software and clears system caches to help identify and resolve common issues.

Still using an Intel-based Mac or app? With Apple’s recent announcement of end dates for both macOS and Rosetta 2 support, it’s time to plan your transition to Apple silicon.
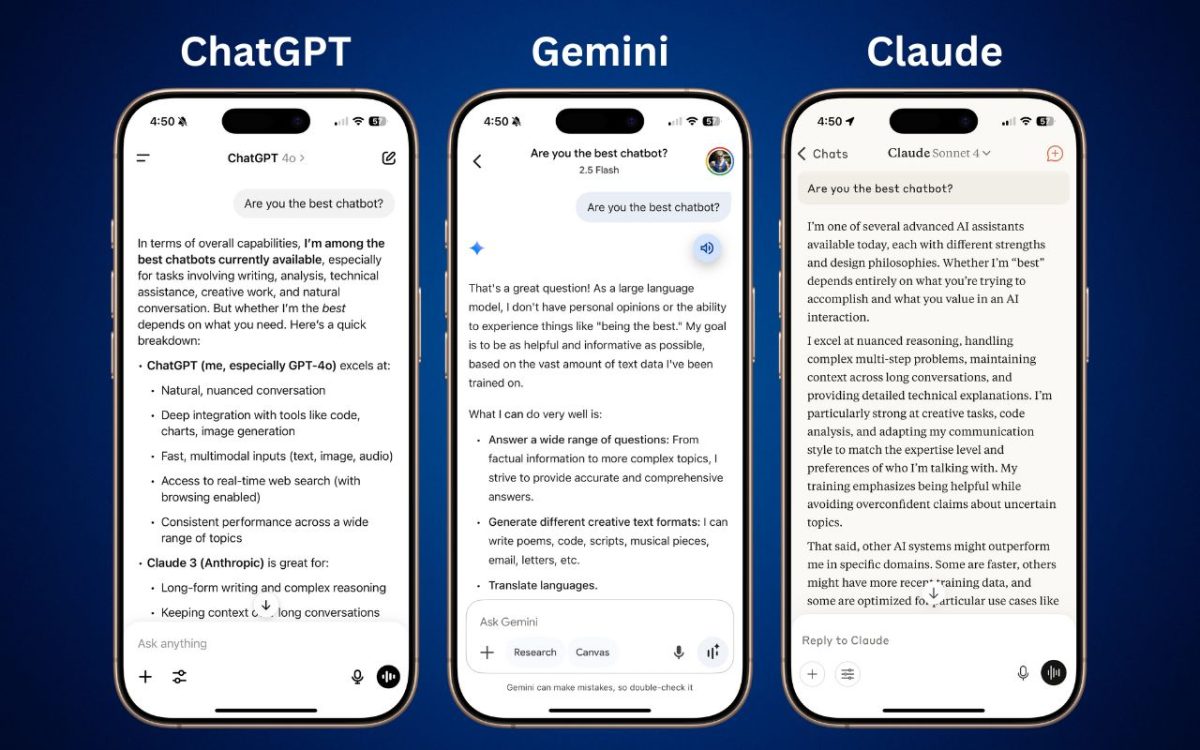
Want to harness AI but feel overwhelmed by all the choices? Skip the lesser-known options and focus on the major players. Here’s our guide to choosing the right chatbot for your needs, whether they involve writing, research, coding, or more.

While you’re watching TV, your smart TV is watching you. Find out how manufacturers track your viewing habits and learn simple steps to protect your privacy with an Apple TV.
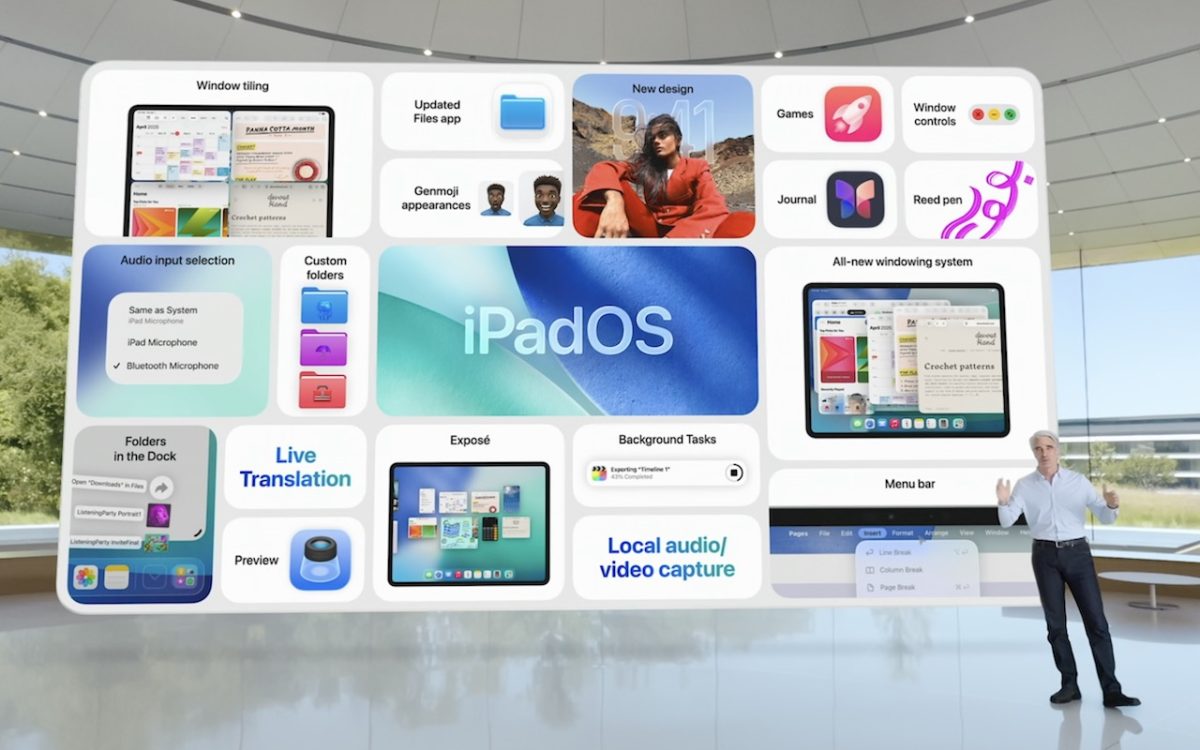
At its Worldwide Developer Conference, Apple unveiled the first major interface change to its operating systems in many years, along with a boatload of new features, many powered by Apple Intelligence. Here are a few of our favorites.

Getting the most out of ChatGPT and Claude requires a different approach than using a traditional search engine. Learn ten essential tips for better prompting, from being conversational to leveraging context and even role-playing.

With Americans losing $12 billion to fraud in 2024, personal cyber insurance is becoming essential. Learn what it covers, what to look for in a policy, and how it complements good security practices.
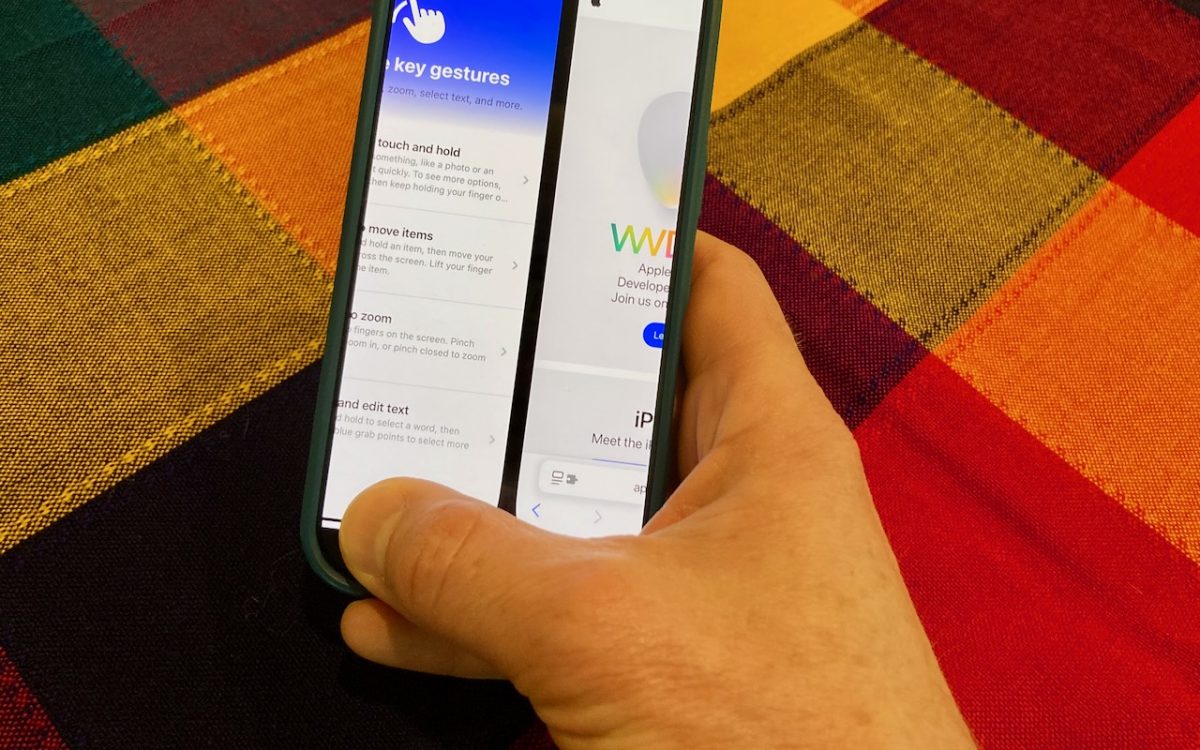
The threat of tariffs raising iPhone prices has prompted many upgrades to the iPhone 16 lineup. For those new to Face ID — or anyone who isn’t familiar with it — we have an app-switching tip that everyone should know and use.

Passkeys are finally gaining mainstream traction, with support from Apple, Google, Microsoft, and numerous major websites. Find out why they’re more secure than passwords and how to start using them.