Hackers have learned how to poison shared chatbot conversations with malware — and get Google to display them in search results. Never trust step-by-step instructions or Terminal commands from user-generated chatbot pages.


Hackers have learned how to poison shared chatbot conversations with malware — and get Google to display them in search results. Never trust step-by-step instructions or Terminal commands from user-generated chatbot pages.

When should you trust an AI chatbot’s tech advice? Learn when chatbots can help with basic issues and when it’s time to call a professional for more complex problems.

A clever new scam masquerades as a CAPTCHA test, asking users to paste text into Terminal to prove they’re human. Instead, it installs malware designed to steal passwords, browser data, and other sensitive information.

With Americans losing $12 billion to fraud in 2024, personal cyber insurance is becoming essential. Learn what it covers, what to look for in a policy, and how it complements good security practices.

Passkeys are finally gaining mainstream traction, with support from Apple, Google, Microsoft, and numerous major websites. Find out why they’re more secure than passwords and how to start using them.

Tired of juggling work and personal tabs in one browser? Learn how browser profiles can keep your online life organized and distraction-free, plus get step-by-step tips for setting them up in Safari, Chrome, and Firefox.
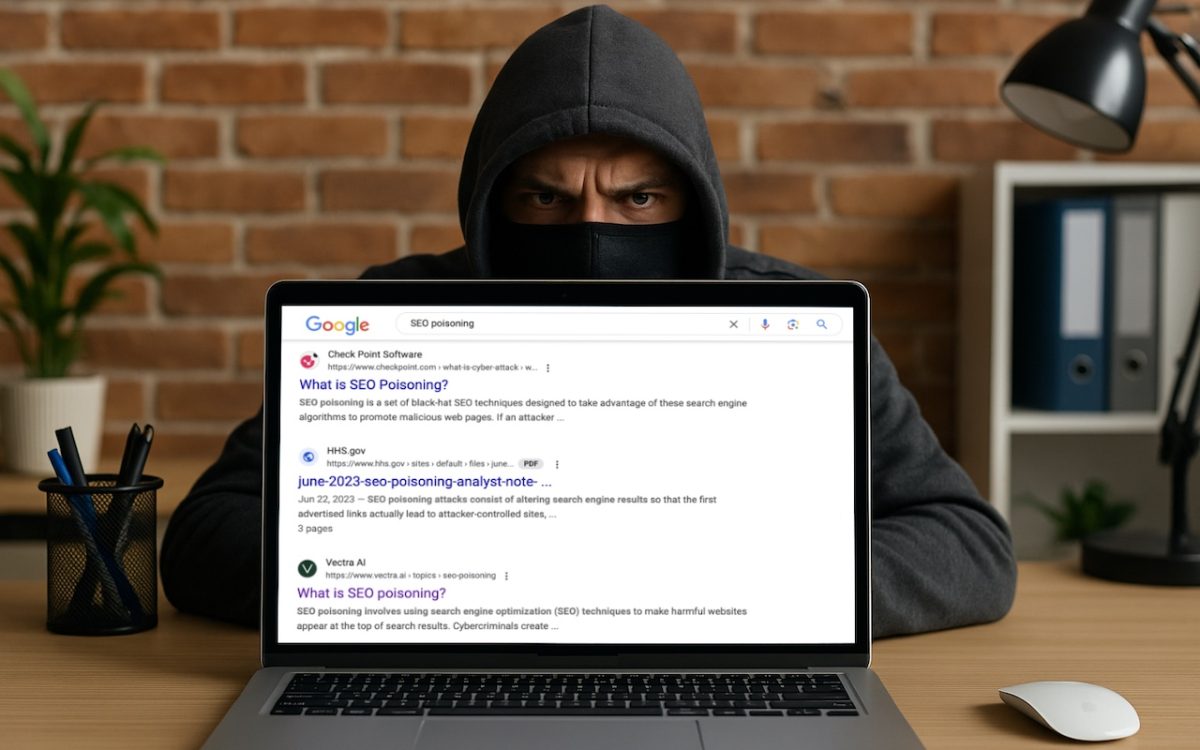
You know that the phrase “I read it on the Internet, so it must be true” is absurd, but you should extend that skepticism to Google search results. We’ve seen two recent instances of malicious content bubbling to the top of searches. Trust but verify.

Security at home is one thing, but what about when you’re on the road? Many of the same precautions apply, but depending on your level of concern and where you’re going, additional techniques can help keep you and your data safe.

If world events have you worried about your online privacy and security, you may be interested in minimizing your exposure. We recommend some simple steps that everyone can take and other actions for those who are especially concerned.

Beware of PayPal invoice scams that might even appear to come from Apple. Should you receive one, report it to PayPal to help protect other people, but don’t mark the message as spam.